e-Discovery, Email Archiving & Audit Software
e-Discovery, Email Archiving, and Audit Software: Streamlining Legal and Compliance Processes
In today’s digital world, organizations are grappling with the ever-increasing volume of electronic data. e-Discovery, Email Archiving, and Audit Software have become indispensable tools for efficiently managing, preserving, and retrieving digital information, particularly in the legal and compliance sectors. This page provides an in-depth overview of these critical software solutions, their applications, benefits, and considerations.
Image One has the ability to help you automate the identification, collection, preservation, and review, of electronic stored information (ESI) for regulatory and legal proceedings, while automating the legal hold notification process. In addition to identification, the e-Discovery tools will help with the deduplication of all files on your network, SharePoint, email, files shares, storage area network (SAN), network attached storage (NAS) and desktop and laptop computers.
e-Discovery: Unearthing Digital Evidence
e-Discovery, short for electronic discovery, is the process of identifying, collecting, and preserving electronically stored information (ESI) as evidence in legal cases or investigations.
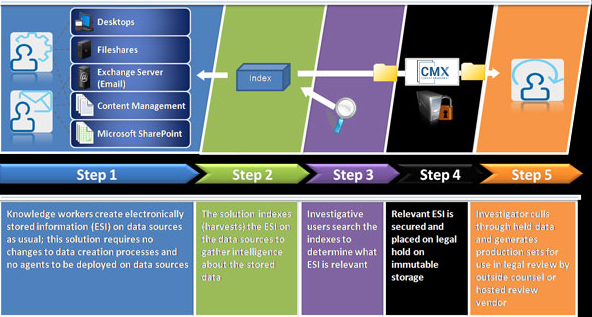
e-Discovery automates electronic storage information (ESI) discovery, bringing in-house the ability to identify, collect, preserve (legal hold), process, analyze, and review policy-based management of unstructured content. Its unique non-invasive footprint will cross discovery platforms of data sources such as file shares, NAS, SAN, desktops, laptops, email, Microsoft SharePoint, content management systems and more. The solution enables your legal and IT teams to respond rapidly and efficiently to today’s business information governance needs, including litigation, investigations, compliance, and audits. In addition, you can proactively discover, classify, manage, identify duplicate files, and preserve information according to business value and risk. Your IT teams will also be able to identify information and duplicate files, offering an easy aid to managing data and files stored on a tiered architecture.
It plays a crucial role in modern litigation and regulatory compliance. Key aspects of e-Discovery include:
- Data Collection: Identifying and collecting relevant data from various sources, including emails, documents, databases, and social media.
- Legal Hold: Implementing legal holds to prevent data deletion or tampering, ensuring data preservation during legal proceedings.
- Data Processing: Analyzing and processing collected data for review, including metadata and text extraction.
- Review and Production: Reviewing and producing relevant documents and information for legal purposes, often involving legal professionals and e-Discovery tools.
- Compliance and Regulatory Reporting: Ensuring compliance with legal and regulatory requirements for data preservation and production.
Email Archiving: Secure and Organized Email Storage
Email Archiving software is designed to capture, store, and organize email communications in a secure and easily retrievable manner. It is particularly valuable for organizations seeking to meet legal and regulatory requirements, maintain data integrity, and enhance email management.
Image One’s offerings of email archive solutions will help reduce operational costs, and backup times while enforcing e-mail record-keeping policies in compliance with internal governance as well as industry and government regulations. Our team implements email solutions which seamlessly allow users to access archived content, eliminating the need to create separate PST files, or set email quotas. You will now have the ability to easily archive a single representation of emails and attachments, while deleting unwanted copies. In addition to providing a secure archival strategy to your emails, our email discovery allows you to gain proactive information management, aiding in efforts around litigation, legal holds, and audit preparation. To ensure secure authorized investigator access, the solution supports EDRM XML export standard for data transfer to e-Discovery processing, analysis and review.
Key aspects of email archiving include:
- Data Capture: Archiving all inbound and outbound emails, attachments, and metadata for retention and retrieval.
- Storage and Organization: Storing emails in a structured, searchable format, often with tagging and indexing capabilities.
- Legal and Regulatory Compliance: Ensuring email archiving practices meet legal, regulatory, and industry-specific requirements.
- Data Preservation: Archiving emails for long-term retention, even as active email accounts are periodically purged or deleted.
- Quick Retrieval: Facilitating rapid and efficient email retrieval, particularly during e-Discovery processes or audits.
- Data Backup and Disaster Recovery: Providing a secure backup of email data to safeguard against data loss due to system failures or cyberattacks.
Audit Software: Ensuring Transparency and Accountability
Audit Software is essential for businesses to conduct internal and external audits, ensuring transparency, accountability, and compliance with established standards and regulations. It encompasses a range of audit-related functions, including:
- Data Collection: Gathering financial and operational data from various sources for audit purposes.
- Data Analysis: Examining collected data to identify discrepancies, errors, or anomalies.
- Report Generation: Creating comprehensive audit reports that provide insights into an organization’s financial health, compliance status, and internal controls.
- Compliance Management: Monitoring and enforcing compliance with internal policies, industry standards, and regulatory requirements.
- Workflow Automation: Automating audit processes to enhance efficiency and reduce manual work.
- Risk Assessment: Identifying potential risks and vulnerabilities within an organization’s operations.
Benefits Your Organization Can See With e-Discovery, Email Archiving & Audit Software Solutions:
- Data Accessibility: Quick and organized retrieval of relevant information for legal cases, audits, or compliance inquiries.
- Cost Reduction: Streamlining data management processes, reducing storage costs, and avoiding costly legal disputes.
- Compliance Assurance: Meeting legal and regulatory requirements for data preservation, transparency, and financial reporting.
- Data Security: Secure storage and protection of sensitive information, safeguarding against data breaches and cyber threats.
- Efficiency: Reducing the time and effort required for data collection, organization, and analysis.
- Risk Mitigation: Identifying and mitigating potential risks and vulnerabilities within an organization.
- Transparency: Ensuring transparency and accountability in business operations and financial reporting.
In summary, e-Discovery, Email Archiving, and Audit Software are essential for organizations seeking efficient data management, legal compliance, and accountability. By implementing these solutions, businesses can navigate the complexities of modern data-driven operations while minimizing risks, reducing costs, and ensuring data integrity.
